Security is also a management of access and identities.
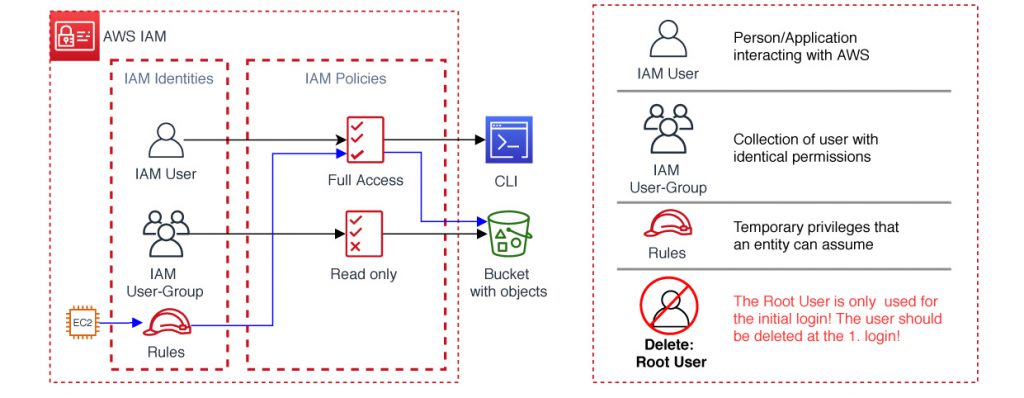
IAM: User, Group, Role
AWS IAM is a core tool of the customer for managing authentication and authorization the cloud environment. Authentication tells, who is entering the account. We can authenticate, if the actor is, who he says he is by using credentials, like passwords, one time passcode or other mechanisms, like MFA Token.
Ones we authenticate a user, it’s relevant to validate the authorization, what privileges are allowed to the user?
Least necessary privileges is the best practice only need to have access not nice to have. The rule configuration is one core customer responsibility. In a holistic view we end in a shared responsibility model.
An IAM User maps to a single person or application interacting with the cloud platform, e.g. a developer, a tester an administrator, an auditor, all named users in my environment, the team.
A Group is helpful, if we have a job group with equal privileges we grant them.
The 3rd access is the Role. It’s only a temporary privileges that an entity can assume. The authentication is used at the CLI, SDK or the AWS MC. E.g. a program written with a SDK can pick up a IAM credential to login to act in relation to the given privileges in the infrastructure.
The list of privileges (IAM policies) is a list of instructions for an authenticated identity that is permitted to use. If the right to use a privilege is explicitly not in the list, it’s implicitly denied.
The IAM Role could be assume from an IAM user, an application or a service. Roles uses an IAM policy for permissions for a temporary time and or a specific event, like a disaster recovery process only. Especially for application authentification it’s relevant, using an IAM role for temporary security credentials.
[Above: EC2 / Rules / Full Access / Store in S3, blue arrow]
Root User
A special IAM User is the Root User, who has full privileges and is the only existing initial user before creating an account. In a brand new account there are no other created Users. First login with the Root User, create an IAM User, grant administrator rights, log out in the role of Root User and never again login as Root User! The idea is to do all operations by named identities and not by a super-user identity like the Root User.
Best practices are:
o Delete access keys for the AWS account root user!
o Activate multi-factor authentication (MFA)
o Only give IAM users persmissions they need
o Use roles for applications
o Rotate credentials regularly
o Remove unnecessary users and credentials
o Monitor activity in your AWS Account, like AWS Inspector